One of the advantages that IP phones have is the ability to create custom applications that can perform any number of functions. PHP and other dynamic web development languages can be used to create a great deal of functionality. The following is a simple application that prints one of three quotes to the phone. PHP or another dynamic language could be used to query databases, websites, etc. for any kind of data you may want accessible from a phone.
The text below was saved as “quote.php” on a PHP enabled web server, and added as a standard XML app. Due to the layout of the blog, you are probably better off copying this into your favorite text editor.
<?php header(‘Content-type: text/xml’); ?> <!– Without this line, the phone will not parse this as XML. Must be the first line of the script –>
<CiscoIPPhoneText> <!– Puts text on the phone screen–>
<Title>Today’s quote is:</Title> <!– This displays on the top, over the main text area–>
<Prompt>Why do you ask?</Prompt> <!– This displays on the bottom, under the main text area–>
<Text> <!– This assigns the actual text on the phone–><!– The PHP function defines an array of quotes, and posts one to the text area–>
<?php
$quote = [“To be or not to be, that is the question”, “Everybody comes to Rick’s”, “Follow the white rabbit”];
$rnum = rand(0,2);
print($quote[$rnum]);
?>
</Text>
<SoftKeyItem> <!– Define a softkey. The ones here are the defaults, and the app doesn’t really need them.–>
<Name>Update</Name> <!– The name that displays–>
<URL>SoftKey:Update</URL> <!– The URL or an action–>
<Position>1</Position> <!– The softkey position–>
</SoftKeyItem>
<SoftKeyItem>
<Name>Exit</Name>
<URL>SoftKey:Exit</URL>
<Position>3</Position>
</SoftKeyItem>
</CiscoIPPhoneText>
The app is added to CUCM as an XML Service:
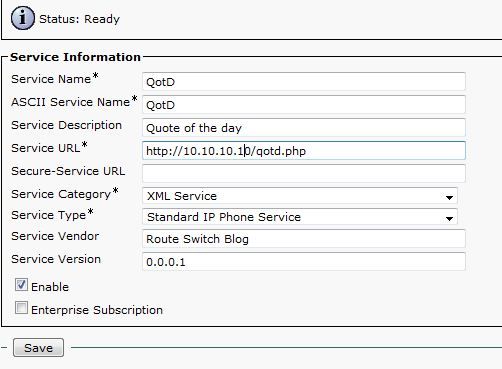
The app on a phone:

Also see: Cisco Unified IP Phone Services Application Development Notes, PHP books at Amazon.com
