PBX administrators are sometimes called on to block calls coming from specific numbers, such as telemarketers or other harassing calls.
Until Communications Manager 8.x, the only way to block incoming calls based on the calling number was to use an H.323 or SIP gateway, and use translation rules on the gateway to reject the number. While there are still good reasons to do this, starting in 8.0, UCM has the ability to block or reroute based on calling number via the “Route Next Hop By Calling Party Number” feature on translation patterns.
Depending on the circumstances, blocking at the gateway may still be your best option, but by configuring it in UCM, you can apply the same blocked numbers to multiple gateways.
The rest of this post, we will build an example of the configuration described in this Technote.
We are assuming a basic setup with all internal phones in a partition called “Internal_DNs_PT,” a gateway with a CSS “Inbound_Routes_CSS” that searches for translations in a partition called “Inbound_Routes_PT”
Call flow for inbound calls:
- PRI to MGCP Gateway
- Receiving 10 digits from Telco
- Translation pattern in “Inbound_Routes_PT” Translates 123555XXXX to XXXX
- CSS “Internal_Routes_CSS” finds 4 Digit DNs in the Internal_DNs_PT.
Goal: Block all inbound calls from (890)555-1212.
Step 1: Create a Partition named “Blocked_Numbers_PT” and CSS named “Block_By_Calling_CSS”.
Step 2: Create a Translation Pattern in “Blocked_Numbers_PT,” with a pattern of “!” to match all calls, and a CSS that includes Internal_DNs_PT. This allows any calls not specifically blocked to be routed. No actual number translations should be performed.
Step 3: Modify the translation pattern in Inbound_Routes_PT to use the Block_By_Calling_CSS, and select the option to “Route Next Hop by Calling Party Number.”
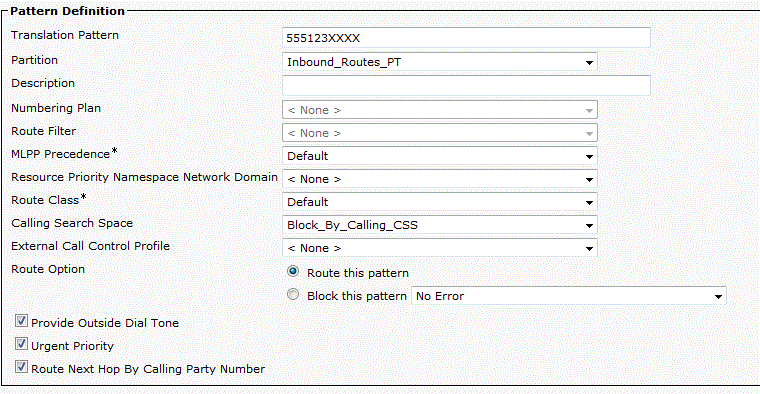 At this point, a call comes in, 10 digits are presented from the Telco, the translation pattern in Inbound_Routes_PT strips the initial digits to leave the 4 digit extension. UCM then looks in Blocked_Numbers_PT, finds the ! pattern, which does not make any changes, but searches Internal_DNs_PT for the extension, and passes the call on.
At this point, a call comes in, 10 digits are presented from the Telco, the translation pattern in Inbound_Routes_PT strips the initial digits to leave the 4 digit extension. UCM then looks in Blocked_Numbers_PT, finds the ! pattern, which does not make any changes, but searches Internal_DNs_PT for the extension, and passes the call on.
Step 4: Create translation patterns in Blocked_Numbers_PT with the number to be blocked as the pattern, remembering to include any access codes, etc. that the number would have at that point, and the Route Option set to Block This Pattern with the error you want.
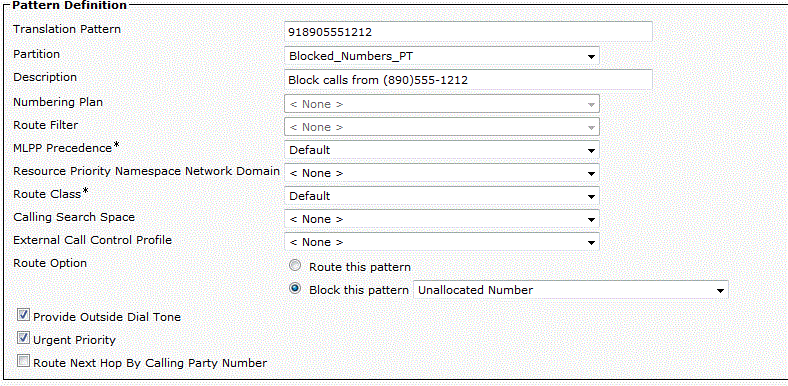
Alternatively, you could translate the called number to a security officer or something similar. I personally want to route one to Unity Connection or a CCX application playing this recording, but I have never gotten the chance to.
Once you have this configured, you can test it by blocking a number you have control over, like your cell phone, and making sure it is blocked.
If you want to only block calls to a specific number, leave the 123555XXXX to XXXX translation pattern using a CSS searching the Internal_DNs_PT, and then create more specific translations that route through the blocking configuration.
For instance, creating a translation pattern for 1235550987 to XXXX using Block_By_Calling_CSS, and the “Route Next Hop by Calling Party Number” option will only block calls to 1235550987 from the numbers in Blocked_Numbers_PT, but allow those numbers to call other DNs. An instance where you might use this if a FAX machine keeps calling a voice line, and you want to prevent those calls while still allowing FAXs to be sent to legitimate FAX machines.
Interested in learning more about CUCM? Check out our other posts here.


